Perimeter monitoring is essential to protect and safeguard physical assets and operations. It serves as the primary defense against intrusion or harmful events.
Efficient and effective perimeter security is crucial, especially in industries working with valuable or sensitive assets in physical space, whether it’s precious metals mining or biodiversity conservation parks.
However, as threats become increasingly sophisticated and complex, traditional perimeter monitoring approaches often fall short, generating significant risk to land and other valuable public or private assets.
Typical Applications of Perimeter Monitoring
Perimeter monitoring is typically used in industries where significant land or critical infrastructure assets are involved.
Examples include transportation hubs like airports and train stations, industrial plants, data centers, military installations, mining pits, oil pipelines, renewable energy generation sites (solar or wind farms), energy transportation lines, natural reserves, and indigenous land.
The primary purpose of perimeter and territorial integrity monitoring is to protect these spaces from unauthorized intrusion, theft, vandalism, or other potential hazards.
Challenges of Traditional Perimeter Monitoring Solutions
.jpg?width=1920&height=1080&name=Blog%20Link%20Preview%20Image%20(23).jpg)
Traditional perimeter monitoring solutions primarily involve physical barriers, alarms, and manual surveillance systems staffed by security guards or forest rangers. However, they come with several inherent challenges:
- Limited Coverage: Most traditional solutions offer limited coverage, usually restricted by the physical boundaries they can cover. This leaves extensive, open areas vulnerable to undetected intrusion or damage, whether at specific times of the day or in perpetuity.
- Human Limitations: Traditional systems often rely heavily on human intervention for surveillance and response. High-value assets are often stolen using information extracted from employees in the know as to their location, transit routes, and times, as well as security weaknesses. This brings about challenges linked to human errors, fatigue, distraction, or in some cases, even corruption and bribery.
- Blind Spots: Every surveillance system has blind spots or areas not covered by cameras or sensors. These can be exploited by nefarious actors intentionally or by chance, leaving assets at higher risk. They can be specific times of the day or the year (e.g., public holidays) when assets or entrances/exits are left unguarded or specific parts of the area that lend themselves more exposed to harm (e.g., natural borders like a mountain range or river vs. artificial man-made borders).
- Delayed Response: Traditional systems can suffer from delayed response times due to the manual processes involved, giving intruders a crucial time advantage to steal, vandalize, and leave unnoticed before anything can be done.
- Vulnerability: Physical security systems can be susceptible to local or remote tampering or disabling through physical interventions or cyber attacks, rendering the entire system ineffective.
- Lack of Insights: Traditional security systems usually need more analytical capabilities to predict patterns or provide actionable insights for proactive threat mitigation. Frequently the most expensive incidents are well planned, with security teams failing to detect signs of individuals scouting the site and its defenses from outside the perimeter. Where the “perimeter” starts and ends is a fuzzy concept, and the most proactive security teams will always seek more visibility than less.
Tools to Enhance Land Asset Protection Strategies
Enhancing land asset protection requires adopting advanced technologies and strategies. Here are some ways to achieve it:
- Integrated systems and AI: Integrating surveillance systems with alarms, access control, and response protocols can reduce response times and increase overall effectiveness. Various companies can help integrate multiple security technologies and systems, ensuring that the whole contributes more than the sum of its parts. More systems usually mean more data, and that’s where AI can come in and help analyze vast amounts of data to classify threats and predict the future based on historical patterns.
- Drones and IoT sensors: Drones can help monitor extensive areas from above, providing a birds-eye view and reaching areas that would otherwise be inaccessible via normal means. Internet of Things (IoT) sensors can provide continuous monitoring and instant alerts when unusual activities are detected. Both are powerful technologies with vast potential but require installation, operation, and maintenance and can be exposed to damage, theft, and tampering.
- Virtual geofences with automatic alerts: Smartphones follow us everywhere, often leaving anonymous traces that can be monitored. Remote sensing technologies such as AKTEK iQ Areas help clients in the energy, timber, and mining industries as well as natural conservation organizations, protect land assets from intrusion, encroachment, theft, and vandalism in new ways that bring more visibility to potential threats. By designing virtual geofences around key assets or weak areas on the perimeter, security teams can be automatically alerted by email or SMS to suspicious activity detected and inform ground teams accordingly, guiding resources to where (and when) they can be most impactful.
Pau Brasil National Park Affected by Illegal Logging
.jpg?width=1920&height=1080&name=Blog%20Link%20Preview%20Image%20(22).jpg) Pau Brasil National Park was created in 1999 as a preservation area in a major biodiversity hotspot and one of Brazil's most degraded biomes: the Atlantic Forest.
Pau Brasil National Park was created in 1999 as a preservation area in a major biodiversity hotspot and one of Brazil's most degraded biomes: the Atlantic Forest.
However, the park has long been the target of intense illegal logging activity, mainly because of the amount of Brazilwood – known as “Pau-Brasil” – within its limits.
This Brazilian timber tree, threatened with extinction since 1992, has been of high interest to illegal loggers because of its high value as a raw material. Famous for producing high-end violin bows, Pau Brasil can be sold for thousands of dollars in Europe and the United States.
Even though illegal logging has occurred in the area since at least 2016, the issue garnered special attention when the Brazilian Federal Police and government agencies found evidence of criminal association activity in the park and official documents stating that the exported wood had originated from the Pau Brasil National Park.
Operation Ibirapitanga II began at the end of 2022 to go after the criminal group.
Even though the operation resulted in several arrests, the issue persists in the area, with the park management receiving constant complaints of traces of illegal presence, as shown between January and March of this year, when they found traces of six bonfires, according to Piauí magazine, showing that traditional security methods to monitor such a big and remote area are not enough to secure it from degrading activities.
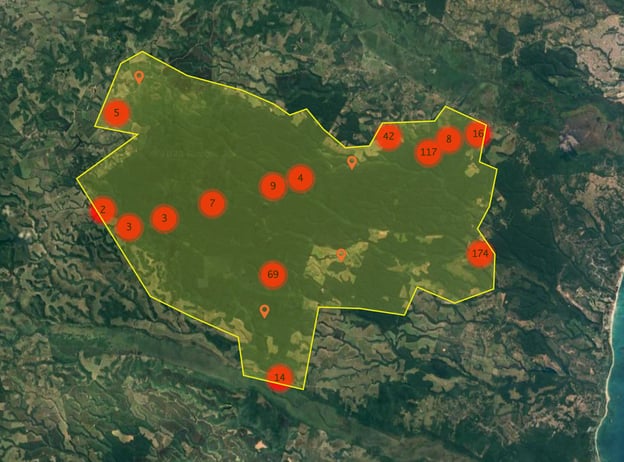
Investigating the issue leveraging iQ Areas, AKTEK saw an increase of 66% in mobile phones observed at night inside the park between March and January 2023, suggesting an increase in intrusions and, as a consequence, illegal logging activity.
We also estimate that night-time activity grew 105% over the period, with clusters in the south near Rio do Trancoso and in the northeast and eastern sections, highlighting areas that need special attention.
This analysis was done remotely and securely, monitoring nearly two hundred square kilometers (47,020 acres) of protected land daily.
This would not be doable with forest rangers, drones, or satellite imagery.
In Summary
Perimeter monitoring has come a long way, but much must be done. As threats evolve, so must our protective measures.
Traditional perimeter monitoring solutions are no longer sufficient.
The industry must embrace technological advancements in remote sensing, AI/machine learning, IoT, and drones to bolster land asset security.
Implementing these advanced solutions means more than preventing physical intrusions or theft.
It also has broader implications for protecting wildlife, preventing environmental degradation, and ensuring the integrity of critical infrastructure.
By investing in these advanced technologies, we can strengthen our defenses and protect what matters most.
Learn more about AKTEK iO for perimeter monitoring and land asset protection here, and contact our team of experts to explore how iQ Areas can assist your organization.



